I’ve been putting some time into trying to improve my intelligence gathering capabilities. Normally we would call this recon during a pen test or OSINT gathering. But I’ve been thinking about it from the perspective of the CIA who refer to it as intelligence gathering. The ideas are basically same: collect information that provides you with some kind of insight into a target.
For a pen test, I want to know information about the subject I’m testing. Maybe it’s network information, or job openings, or list of employees, all this type of data can be used during later phases of the assessment. For your organization, you may want to know when Anon is going to be launching an attack on your network or an employee who is leaking company secrets on her Facebook account.
OSINT Meets OPSEC
For the CIA, intel operations are part of operational security. The intel may tell you when future attacks are planned, secret ways terrorist organizations are communicating, or weaknesses in your adversaries. These same types of operations can be applied into your own OPSEC model: Looking for discussion about future attacks on your organization, useful information about your competitors that was accidentally leaked, potential vulnerabilities in your own systems that become publicly available.
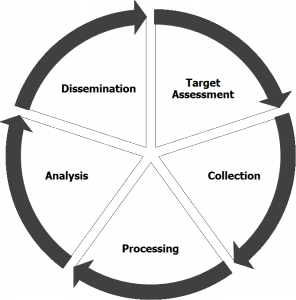
This is what the cycle look like in the most generic form. There’s a lot of explanation that has to go into each phase but I think you can interpret each however you’d like.
This cycle has many different versions. It seems like different governments interpret it in different ways but they all basically stem from this image above. People have also been applying the intelligence lifecycle to APT (yes.. I said it…) because it directly applies to targeted network attacks. Here’s a good one from a hacker organization called “Dell”:
The CIA and You?
The Dell image is cute, but is meant to only highlight a small portion of the potential sources that the CIA documents. But in general, some books say there are four primary sources of intelligence:
- HUMINT: Information collected from a human source
- TECHINT: Information collected by technical means (APT OMG!)
- OSINT: Open source intelligence gathering
- Direct Action: Hiring an effing milita to take the data.
This is from the CIA’s point-of-view so I’m not suggesting that people should go and steal intelligence from your friends by gun point, or hacking into their laptops, nor am I suggesting looking for human sources of intelligence to turn into spies for you. I’m trying to highlight a model of intel gathering that may improve your skills and capabilities especially when working in groups. Red-teaming for example**. **
I also want to point out that whether it’s the CIA, malware writers, APT-OMGZ! hackers, or corporate spies, the same model basically applies to any types of people with similar goals. Target, collect, process, analyse, disseminate, repeat.
While I’m not talking out-of-my-ass on the subject, I admit I have a lot to learn especially compared to those that are in the intelligence community now. I’ll be giving a presentation about the subject at the next Rochester 2600 meeting this week.