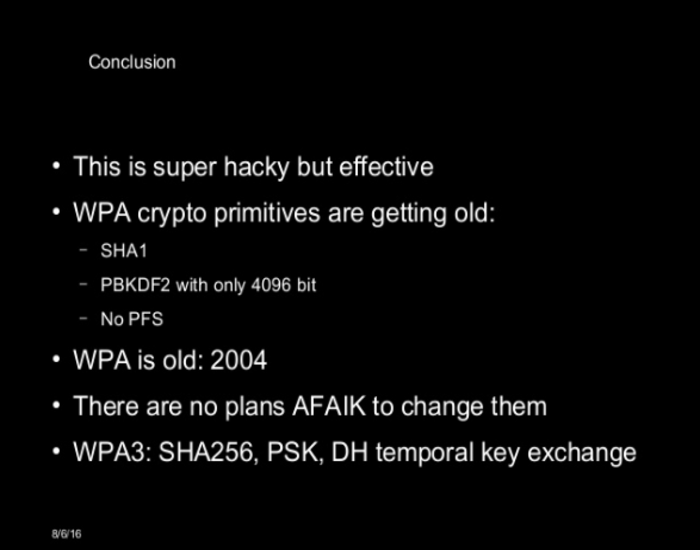
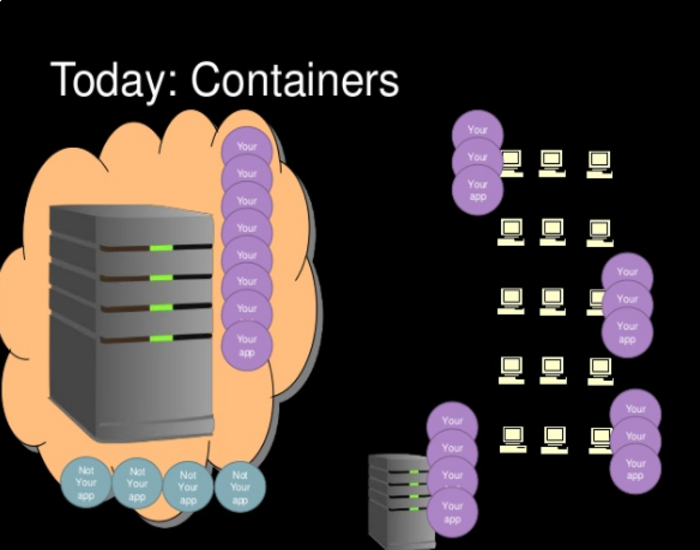
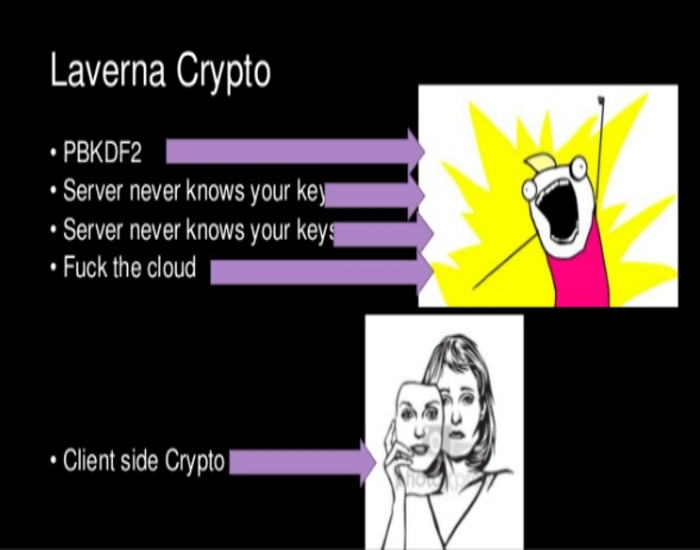
K8s - Pods to root in minutes
A short demonstration for Rochester 2600 exploiting Kubernetes ABAC authentication to compromise a cluster.
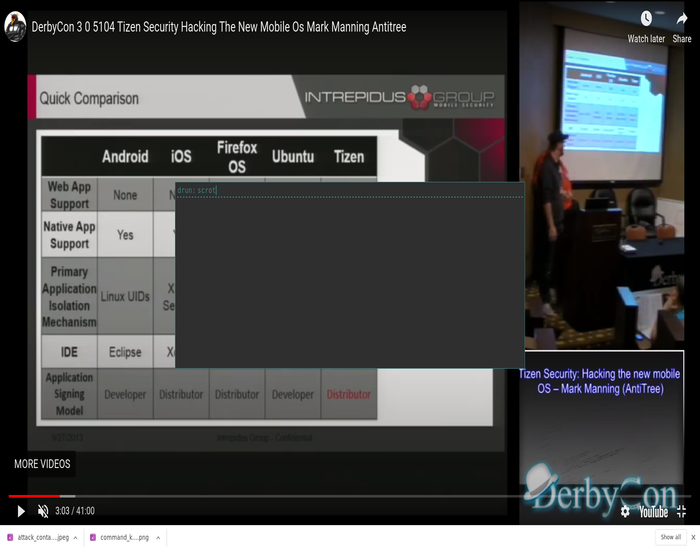
Tizen: Hacking the next modern mobile OS
A talk from 2013 on Tizen hacking and security controls.

The Attrocities of Desktop Keyrings
This was the output of spending time assessing gnome-keyring security controls and looking at other keyrings like Windows and MacOS.
Web Browsing Like It's 1984
A local presentation on the security controls of modern browser extensions comparing Firefox to Chrome and others.
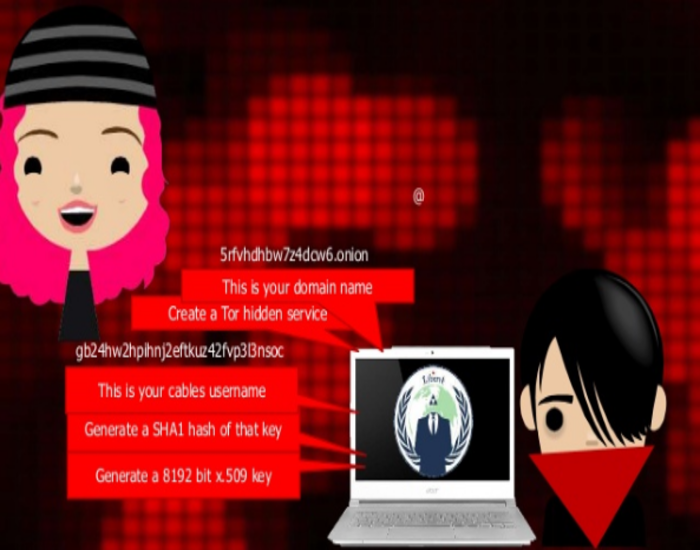
Liberte & Cables vs TAILS & Bitmessage
A comparision between TAILS and Liberte which were then the state-of-the-art for a secure desktop.