Chutney is a tool designed to let you build your own private Tor network instance in minutes. It does so by using configuration templates of directory authorities, bridges, relays, clients, and a variety of combinations in between. It comes with a few examples to get you started. Executing this command, for example
./chutney configure networks/basic
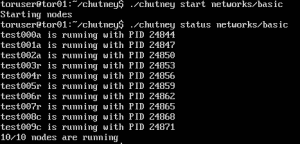
will build a ten client network made up of three directory authorities, five relays, and two clients. Each of which have their own TORRC file, their own logs, and in the case of the relays and authorities, their own private keys. Starting them all up is as easy as
./chutney start networks/basic
So bam! You’ve created a Tor network in less than a few minutes. One item to note, the configuration options in the latest version of Chutney use initiatives like “TestingV3AuthInitialVotingInterval” which require you to have a current version of Tor. In my case, I compiled Tor from source to make sure it included these options.
Building custom torrc files
It’s first job during configuration is to build a bunch of torrc files to your specification. If you tell it you’d like to have a bridge as one of your nodes, it will use the bridge template on file, to create a custom instance of a bridge. It will automatically name it with a four digit hexadecimal value, set the custom configuration options you’ve dictated, and place it into its own directory under net/nodes/.
The very useful part here is that it builds an environment that is already designed to connect between one-another. When you create a client, that client is configured to use the directory authorities that you’ve already built and that directory authority is configured to serve information about the relays you’ve built. The real value here is that if you were to do this manually, you’d be left to the time consuming process of manually configuring each of these configuration files on your own. Do-able, but prone to human errors.
Running multiples instances of Tor
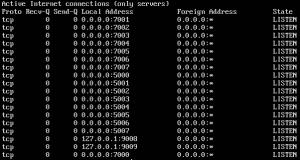
Chutney builds a private Tor network instance by executing separate Tor processes on the same box. Each node is configured to specifically be hosted on a certain port, so for a ten node network, you can expect 20 more more ports being used by the processes.
 Use case
Use case
Chutney is perfect for quickly spinning up a private Tor network to test the latest exploit, learn how the Tor software works, or just muck around with various configurations. Compared to Shadow which focuses more on simulating network events at a large scale, Chutney is more of a real-world emulator. One weakness is that it is not a one-to-one relationship between The Tor Network’s threat model and a Chutney configured one. For example, the entire network is running on a single box so exploiting one instance of Tor would most likely result in the entire network being compromised. That being said, depending on your needs, it offers a great way of building a test environment at home with limited processing power. It’s still a rough-cut tool and it sounds like NickM is looking for contributors.